Configure LDAP authentication on netscaler
Website Visitors:some or all steps are required to add external authentication on netscaler 12 and above:
- Create LDAP Server (authentication server).
- Create LDAP policy.
- Bind the LDAP policy globally.
- Add AD groups to netscaler to restrict access to management access. Optional
- Restrict normal users to netscaler gateway. Optional
Create LDAP Server (authentication server):
To create LDAP server follow below steps. This LDAP server can be used for authentication for all users who login to netscaler portal (netscaler gateway) and for administrators who can login to netscaler management ip for admin purposes. For both the cases LDAP server is common as we are going to use BindDN as default users OU and search filter empty. If BindDN is pointing to any one particular OU, netscaler searches for users in that OU only. Here we used default users group. So, this LDAP server can be used for both above cases explained above.
- Click System > Authentication > Basic Policies > LDAP > Policies Configure parameters for LDAP server as shown below:
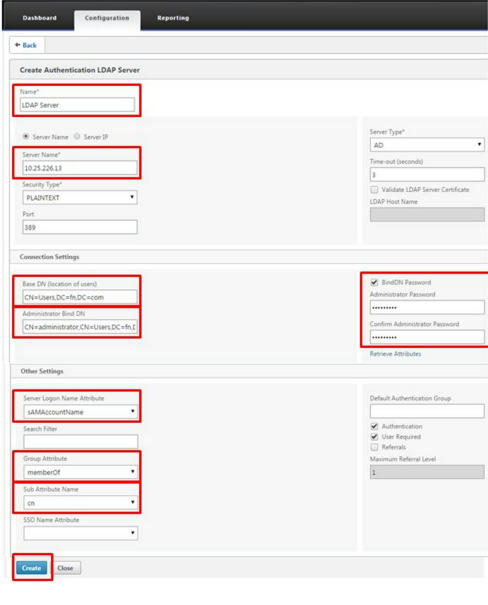
- Specify the required information to define the LDAP Server. Note: On Netscaler 12 and above, you have option called Test LDAP Reachability using which you can test if the parameters entered are correct. The required fields are:
- Name* - Name of the server.
- Authentication Type - The authentication type, in this scenario is LDAP.
- Server – The IP address and TCP port used by the LDAP server.
- Base DN – The base, or node from where the ldapsearch should start.
- Bind DN – The full distinguished name that is used to bind to the LDAP server. This can be admin@domain.com or cn=admin,cn=users,dc=citrix,dc=lab format.
- Bind DN Password – The password for the Bind DN account.
- Confirm Bind DN Password – The password for the Bind DN account.
- Login Name – The name attribute used by the NetScaler appliance to query the external LDAP server or an Active Directory.
- Search Filter – The string to be combined with the default LDAP user search string to form the value.
- Group Attribute Name – The Attribute name for group extraction from LDAP server.
- Sub Attribute Name – The Sub Attribute name for group extraction from LDAP server.
- Security Type – Select Plaintext for non-secure LDAP communication or select TLS or SSL for secure LDAP communication. Note: If you want to use this LDAP server for netscaler gateway for all users, leave search filter empty. If you want to use this LDAP server only to search users in some AD group, use search filter. Value used for this example is &(memberof=CN=NSG_Admin,OU=AdminGroups,DC=Citrix,DC=lab)
- Click Create.
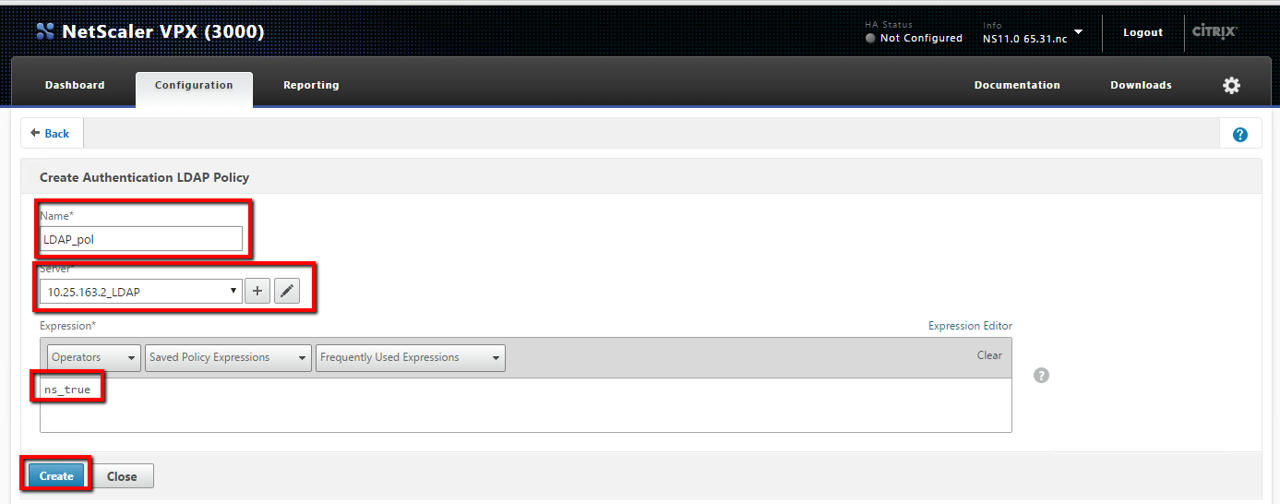
- Click the Policies tab in same page, then click the Add button:
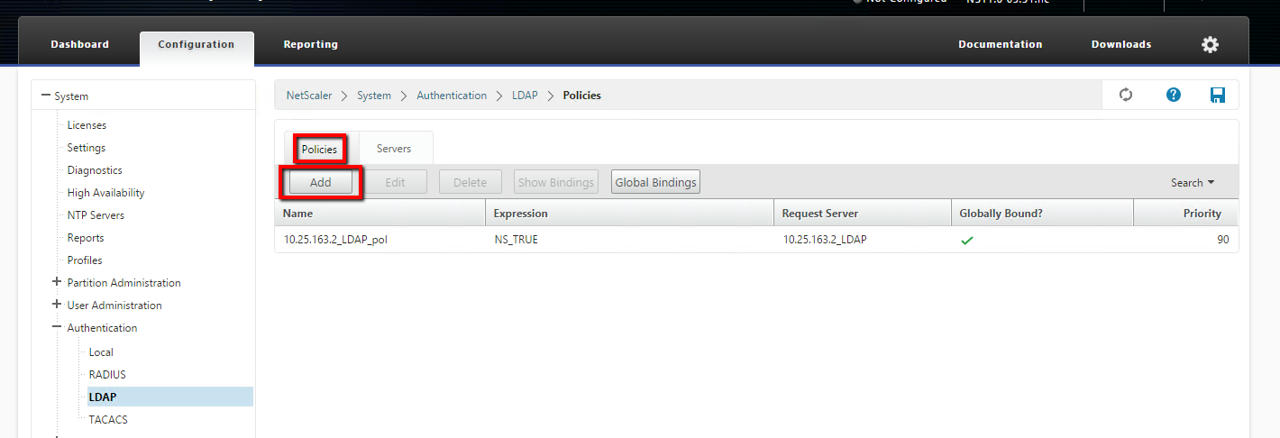
- Enter a name for the policy, select the server that you created in steps 2 and 3 from the drop-down menu.
- In the Expression text field, type ns_true, then click Create:
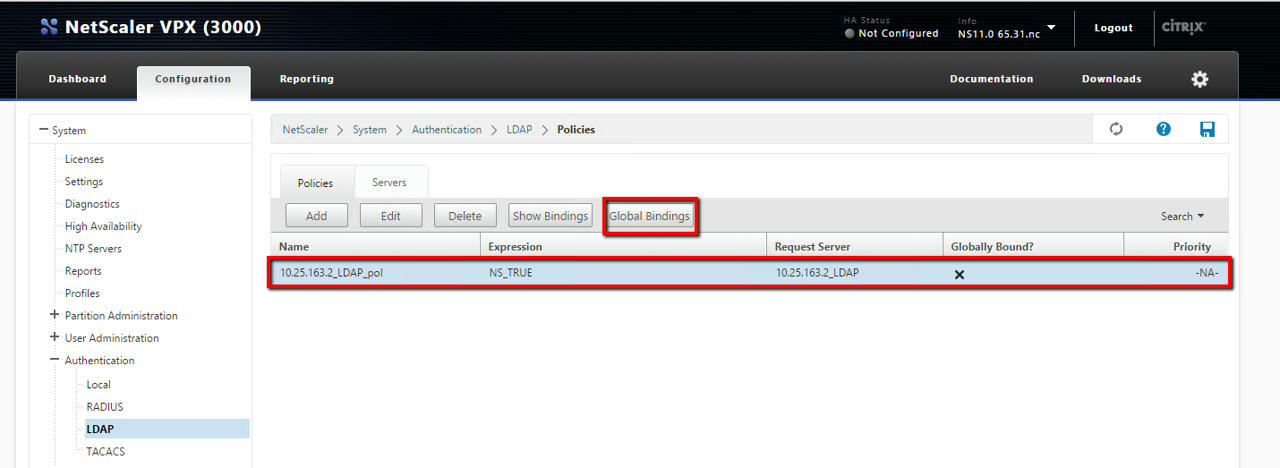
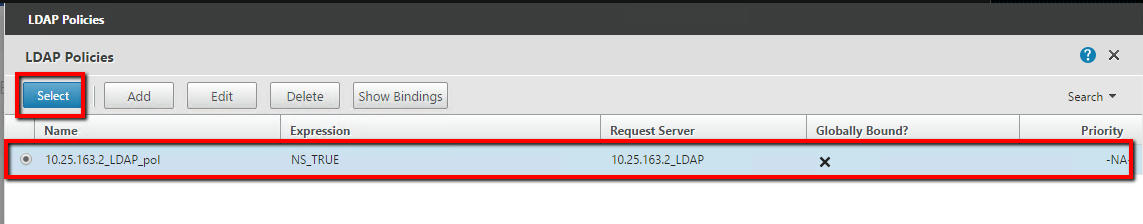
- Click the policy that you just created to select it, then click the Global Bindings button:

- Select the policy that you previously created from the drop-down menu, then click the Select button:

- Click Bind, then click Done.
How to Restrict Access to NetScaler Gateway for only Members of one Active Directory Group
Restricting through LDAP:
- Create LDAP server as explained above. In search filter column (available under server logon name attribute), enter your AD group name in format, memberOf=CN=Citrix Remote,OU=Citrix,DC=corp,DC=local (In dsa.msc, enable advanced features in view menu, and goto the AD group, properties, goto attribute editor column and double click distinguishedName column and get the value.)and save.
- Nested Groups - By default, NetScaler will only search for usernames that are direct members of the Active Directory group. If you want to search nested groups, then add the Microsoft OID :1.2.840.113556.1.4.1941: to the LDAP Search Filter. The OID is inserted between memberOf and = as shown below: memberOf:1.2.840.113556.1.4.1941:=CN=Citrix Remote,OU=Citrix,DC=corp,DC=local
- Click OK to finish editing the LDAP Server.
Now, user can only login if he is part of that particular group.
Restricting through AD Group:
In this scenario, users who are member of you Active Directory group configured in the search filter (Ex, NSG_Admin) will be able to connect to the NetScaler Management interface and will have superuser command policy.
Add a new system group to the NetScaler, under System > User Administration > Groups. This will define the Active Directory group that the users are members of and the Command Policy level that should be associated to the account when logging in. Then, click Create. Note: The Group Name has to match the Active Directory record exactly.
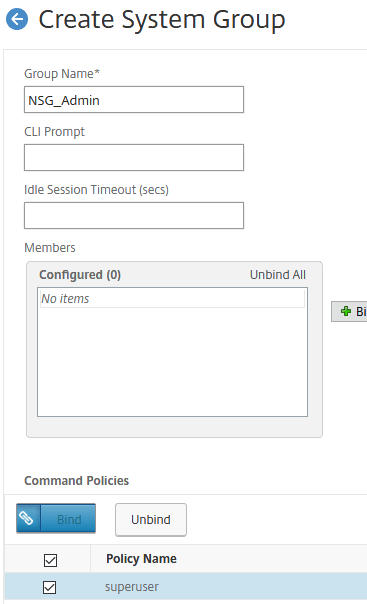
Just add users who need admin access on netscaler to this AD group.
Notes:
- Create ldap server without search filter so that it can be used for all users and admins. If you want to restrict users to netscaler gateway, use above restricting through ldap way. If you want admins to have restricted access on netscaler for management purpose, use restricting through AD group way.
Resources:
Want to learn more on Citrix Automations and solutions???
Subscribe to get our latest content by email.