Utilizing Both SamAccountName and UserPrincipalName for Netscaler Gateway Logon
Enable user login with samAccountName and UserPrincipalName on Netscaler Gateway
Website Visitors:This article explains the steps on how to login to netscaler using userPrincipalName instead of samAccountName or both at same time. If you follow these steps you can use sAMAccountName and userPrincipalName at Same Time for User Logon with Active Directory.
Configuration
By default when you configure netscaler gateway, you would configure it to use userid which is samAccountName. Users enter their userid (like john.doe) and login to netscaler gateway. In this case, you will create an LDAP server with samAccountName as shown below.
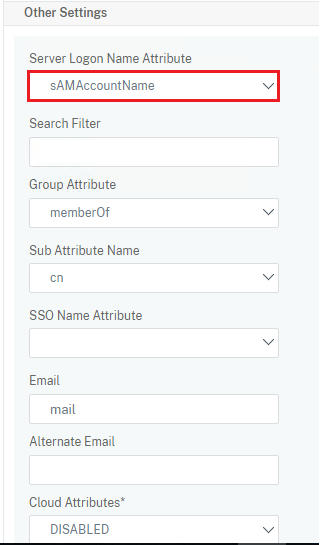
When configured like this, users cannot login to netscaler gateway url with their userprincipalname, which will be in the format john.doe@company.com. Don’t get confused this with an email address. Email and UPN formats look like the same but they are different.
If you want users to use their userprincipalname (which is same as their email) to login to netscaler gateway, create another LDAP server profile and a LDAP server(you can copy the LDAP server you created for samAccountName).
In this second LDAP server which you want to use for userPrincipalName, enter details as shown below. Under Server Logon Name Attribute enter userPrincipalName and for SSO Name Attribute enter sAMAccountName value.
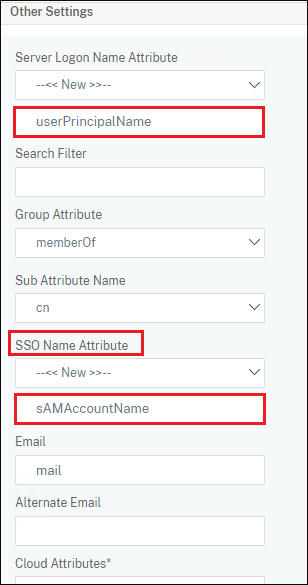
Create two policies for these two LDAP servers. Finally you will have two LDAP servers and two policies related to these LDAP servers.
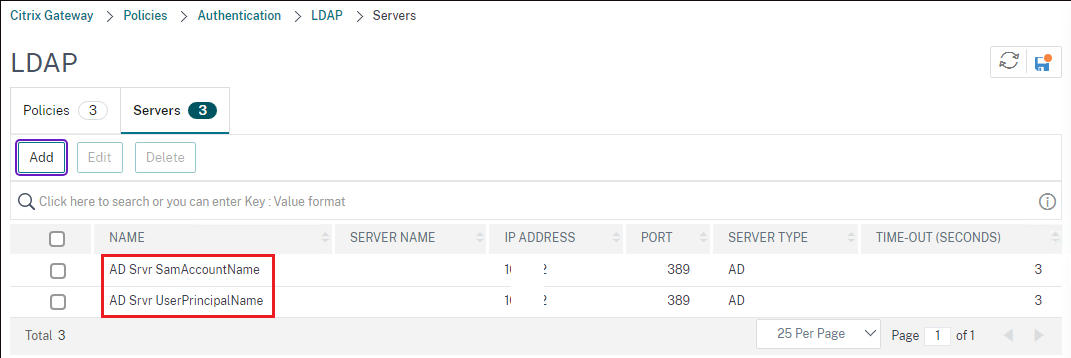
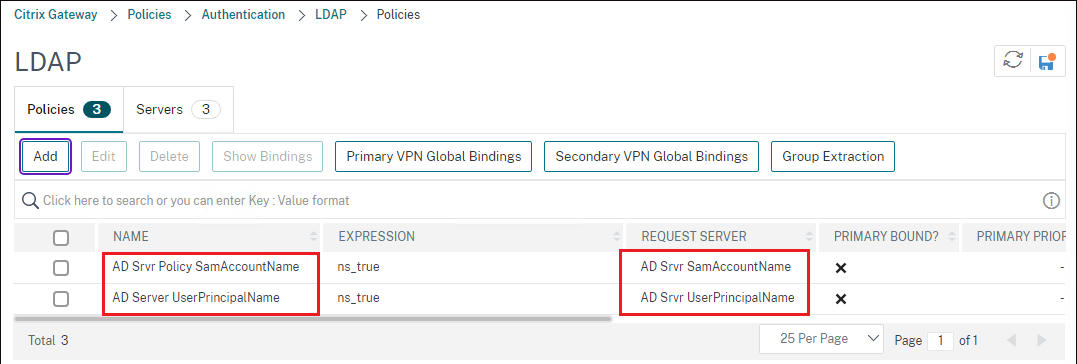
Next add these two LDAP policies to your citrix gateway VIP with different priorities.

If you want to use only UserPrincipalName instead of sAMAccountName add the LDAP policy for samAccountName to your Citrix gateway and remove sAMAccountName LDAP policy from your Citrix gateway. If you want to use sAMAccountName to login, add sAMAccountName LDAP policy and remove UserPrincipalName LDAP policy from your citrix gateway.
When the user tries to login with ‘domain\username’, they will be authenticated by the LDAP profile using ‘sAMAccountName’. And when they uses their email id, they will be allowed by the other LDAP profile. “Server Logon Name” is what the user enters(sAMAccountName) while logging into the gateway authentication page and “SSO Name Attribute” is what is sent to the backend server(userPrincipalName) for the SSO.
You can test this by logging into citrix gateway url with your userid (samAccountName) and UserPrincipalName.
Some articles says remove domain name from session profile but it did not work for me. When I removed SSO domain name from storefront and session profile, I have ended up in errors.
Errors And Solutions
Error1:
When you enter credentials at netscaler gateway, you’d see user not found error. If you run aaad.debug you can see the error in netscaler putty session as well.
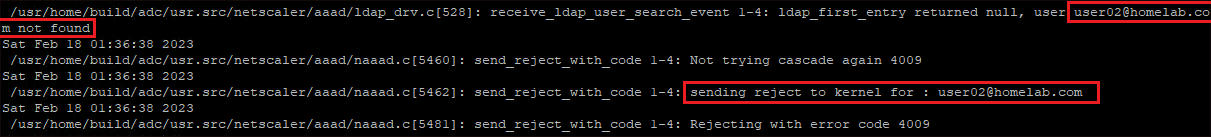
Solution:
Check in user’s AD properties if UPN is updated correctly. If you are using Active directory users and computers, enable advanced features option in view menu and open properties of an AD user. Goto Attribute editor option and scroll down till you find userPrincipalName option. This UPN value should be entered correctly.
If you’d like to use PowerShell, run below command on powershell console. This command will show userprincipalname.
|
|
Error 2:
After logging in at citrix gateway, you’d see cannot complete your request message.
Check in storefront logs. You will find below errors.
Event id: 10
A CitrixAGBasic Login request has failed.
immediately followed by Event id: 7
CitrixAGBasic single sign-on failed because the credentials failed verification with reason: FailedMissingDomain.
The credentials supplied were;
user: userid
domain:
Solution:
Make sure you have domain name in any of the below configurations:
-
In session policy - Check the session policy in your netscaler gateway vip. Edit your web profile. Goto Published Applications tab. Under Single Sign-On Domain enter your domain name.
-
Storefront authentication - Manage Authentication methods in storefront, username and password, Add your domain name. Or in same page, under pass-through from netscaler gateway, enter your domain name under configure trusted domains option.
Error 3:
Event id: 10
A CitrixAGBasic Login request has failed.
immediately followed by event id: 7
CitrixAGBasic single sign-on failed because the credentials failed verification with reason: FailedPasswordComplexity.
The credentials supplied were;
user: user01
domain: DomainName
Solution:
- Add domain name (without extension like .com or .org in your domain name) in netscaler gateway session policy for web.
- Goto storefront select your store, click manage authentication methods, click settings option for Username and password, click Configure Trusted domains. Select Trusted domains only option and add the same domain name you’ve entered in your citrix gateway session profile. Select it as default domain.
- In same manage authentication methods page, click settings option for pass-through from citrix gateway option, select configure delegated authentication and check box for Fully delegate credential validation to citrix gateway option.
References:
How to Pass Domain Information Along with Username to LDAP Server from NetScaler (citrix.com)
Want to learn more on Citrix Automations and solutions???
Subscribe to get our latest content by email.